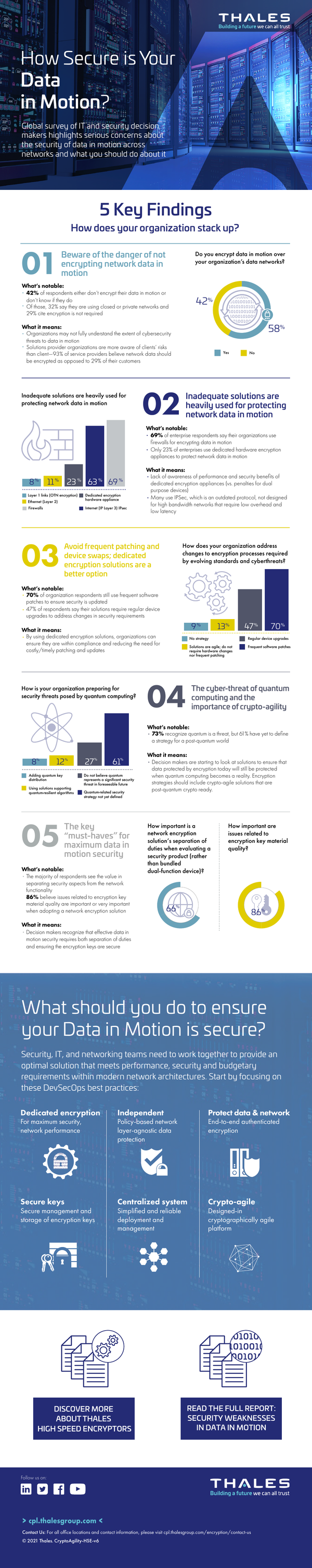
THALES HIGH-SPEED ENCRYPTORS
Unlock the Power of Secure Network Encryption!
As data moves, its safety can be at risk. Do you know where your data travels or how exposed it might be? Try our quick quiz to gain insight into your data journey and get a FREE ebook on how High-Speed Encryptor (HSE) can help your business.

High-Speed Network Encryption eBook
A collection of use cases for various verticals, including:
- Government
- Financial Services
- High-Tech
- Critical Infrastructure
- Healthcare
Download High-Speed Network Encryption eBook to secure data in motion
IDM DACH 2024
Discover the leading innovations shaping CIAM
7 MARCH 2024 | FRANKFURT
Mar 7, 2024 00:00:00
Days43
Hours09
Minutes33
Seconds41
2023 Year in Recap
Thales Identity and Access Management
Visit Thales OneWelcome at Gartner Identity & Access Management Summit
4-5 March, 2024 | London, UK
Visit Thales OneWelcome at
Gartner Identity & Access
Management Summit
4-5 March, 2024 | London, UK
Daily challenges like ransomware, data sprawl, insider threats and regulatory violations, are often tackled with unconnected, siloed tools. This increases risks, complexities, and total cost of ownership.
With that, our mission is clear: to provide you with complete visibility and control over your sensitive data and all paths to it, securing it confidently from its creation and across its lifecycle.
What are the challenges associated with Data in Motion Security?
In today's interconnected world, data flow is essential for business, yet it poses significant security challenges. It is important that we tackle top concerns in Data in Motion security, ensuring your information stays confidential, integral, and accessible only to authorised parties as it moves across networks.
A winning combination for customers
Listen to Sebastien Cano, SVP, Thales Cloud Protection & Licensing, as he shares exclusive insights into the added benefits Thales can offer you.
BOOK A MEETINGA winning combination for customers
Listen to Sebastien Cano, SVP, Thales Cloud Protection & Licensing, as he shares exclusive insights into the added benefits Thales can offer you.
BOOK A MEETINGA winning combination for customers
Listen to Sebastien Cano, SVP, Thales Cloud Protection & Licensing, as he shares exclusive insights into the added benefits Thales can offer you.
BOOK A MEETINGA winning combination for customers
Listen to Sebastien Cano, SVP, Thales Cloud Protection & Licensing, as he shares exclusive insights into the added benefits Thales can offer you.
BOOK A MEETINGAgenda
| Table Header | Table Header |
|---|---|
| 09:00 - 10:00 | Name of the event Lorem ipsum dolor sit amet, consectetur adipiscing elit. |
| 10:00 - 11:00 | Name of the event Lorem ipsum dolor sit amet, consectetur adipiscing elit. |
Venue

QEII Centre, London
The Queen Elizabeth II Centre (QEII Centre) is a conference facility located in the City of Westminster, London, close to the Houses of Parliament, Westminster Abbey, Central Hall Westminster and Parliament Square.
Address: Broad Sanctuary, London SW1P 3EE, United Kingdom
Watch the video!
This 1-minute video shows why Thales High Speed Encryptors (HSE) are far superior to IPSEC tunnels. Make better security, better performance, and easy setup and management.
Why Thales?
Security Expertise
Thales excels in robust network security
Performance
Rapid encryption without compromising data transfer
Compliance
Meets strict regulations for data protection
Leading a new era in cybersecurity with a combined product portfolio
Versatility
Crypto-Agile solutions for diverse security needs
Key Management
Advanced handling of cryptographic key security
Integration Capabilities
Seamless integration with existing IT ecosystems
Leading a new era in cybersecurity with a combined product portfolio
Application Security
We protect modern and hybrid applications against advanced and multi-vector attacks regardless of where they are running.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Application Security
We protect modern and hybrid applications against advanced and multi-vector attacks regardless of where they are running.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Application Security
We protect modern and hybrid applications against advanced and multi-vector attacks regardless of where they are running.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Application Security
We protect modern and hybrid applications against advanced and multi-vector attacks regardless of where they are running.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Identity Proofing
Ensure online users are who they claim to be, and protect against identity fraud.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Identity Proofing
Ensure online users are who they claim to be, and protect against identity fraud.
BOOK A MEETINGIdentity & Access Management
Seamless, secure and trusted access online for customers, employees and partners.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Data Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGLeading a new era in cybersecurity with a combined product portfolio
Data Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGData Security
We redefine how sensitive data is secured from knowing where it is, who has access to it, and when abuse occurs in real-time, to protecting it in all environments whether at rest, in motion, or in use.
BOOK A MEETINGTwo award-winning leaders join forces

Thales Wins Google Cloud Technology Partner of the Year Security
BOOK A MEETING
Imperva Named an API Security & Management Overall Leader
BOOK A MEETING
Data Protection on Demand Wins Cybersecurity Excellence Award
BOOK A MEETINGDiscover More
Protecting Your Data, Every Step of the Way.
Our Venue
How Thales HSE can help?
Trusted Security
Preferred by market leading financial institutions, telcos and other commercial organisations and governments in more than 35 countries with certified FIPS 140-2 L3, Common Criteria, NATO and DoDIN APL.
Maximum Network Performance
Delivers max uptime in the most demanding, performance intensive environments with near-zero latency, and operate in full-duplex mode at full line speed.
Optimal Flexibility
Offers flexible, vendor agnostic interoperability, compatible with all the leading network vendors throughout your network. It range supports network speeds of 100 Mbps to 100 Gbps and single to multi-port appliances and virtual solutions.
A good and solid solution in constant evolution: We’ve been using the Thales OneWelcome Identity Platform to offer 1.3 million customers a simple and secure connection to our websites and mobile application since December 2020."
—Our customer at Gartner®
- Forming Your Encryption Strategy:
Set your vision, know your stakeholders, and assess technologies
- Encryption Deployments & Methods:
Understand encryption and key management techniques
- Post deployment areas to watch:
Be ready for new technologies, regulations and business changes
Schedule a meeting
THALES HIGH-SPEED ENCRYPTORS
Unlock the Power of Secure Network Encryption!
As data moves, its safety can be at risk. Do you know where your data travels or how exposed it might be? Try our quick quiz to gain insight into your data journey and get a FREE ebook on how High-Speed Encryptor (HSE) can help your business.
Question 1 of 3
Do you have data in motion or IPSec?
YesNo
Question 2 of 3
Is the data encrypted?
YesNo
Question 3 of 3
Do you have any plans to encrypt data in motion?
Are you happy for those outside of your business to access your data?
YesNo
Results
Great! But are you completely happy with your encryption solution?
For example, is your network providing the performance you need while ensuring your data in motion is secure?
By dropping in Thales High Speed Encryptors (HSE) you can benefit from the network performance your organization demands without any fork lift upgrades, compatible with the leading networking vendors you may have in your stack.
FACT:
Data in motion, also referred to as data in transit or data in flight, is a process in which digital information is transported between locations either within or between computer systems. Data in motion is one of the three different states of data; the others are data at rest and data in use.








Certified FIPS 140-2 L3, Common Criteria, NATO, UC APL, Thales Network Encryptors are preferred by market leading financial institutions, telcos and other commercial organisations and governments in more than 35 countries. Proven to deliver max uptime in the most demanding, performance intensive environments. The solutions have near-zero latency and can operate in full-duplex mode at full line speed with flexible, vendor agnostic interoperability.

Secure sensitive data and critical applications with centralized storage, protection, and management of cryptographic keys with Thales HSM solutions.
1) SafeNet Luna HSM - Tamper-proof, hardware- based solution available in a wide range of form factors and performance options for high assurance encryption key protection
2) SafeNet Cloud HSM - Cloud-based HSM solution available as-a-service through SafeNet Data Protection On Demand

The market’s most comprehensive data security offering
Our consolidated offering covers the entire spectrum of your data security needs, including:
- real-time visibility into your data activity
- access permissions monitoring
- smart risk intelligence
- in-depth defense across your entire security stack

The market’s most comprehensive data security offering
Our consolidated offering covers the entire spectrum of your data security needs, including:
- real-time visibility into your data activity
- access permissions monitoring
- smart risk intelligence
- in-depth defense across your entire security stack

Quote, Lorem ipsum dolor sit amet, consectetur adipiscing elit. Vestibulum sed lectus et nunc."
—Full Name and Job Title

Swift deployment with a secure, scalable B2B IAM solution
Experience quick deployment in just a few weeks. Our purpose-built, cloud-based B2B IAM solution caters to all your B2B user groups, delivering unmatched security, scalability, and ease of use for seamless collaboration across your B2B ecosystem
Managing Identities and Access for your Business Ecosystem
The only true B2B IAM solution to streamline collaboration and enhance security
Access the InsightsThe Power of Effective B2B Identity Management
Establish seamless collaboration and a scalable B2B ecosystem
Get the ebookDelegation User Management
End-to-end delegated user management for any B2B use case
Get the solution briefEmbrace B2B Identity Management to Minimize Third Party Access Risks
Discover a new approach to addressing modern B2B and B2B2C IAM challenges
Watch on-demandRecursos
Lee más sobre nuestra garantía de ciberseguridad y experiencia en gestión de datos.
La pandemia de ciberataques a la industria farmacéutica
Logrando privacidad y protección de propiedad intelectual mientras se acelera la innovación.
Access the InsightsUn ancla de confianza en un mundo digital
Aborda las brechas en la seguridad de dispositivos médicos, reduce riesgos y crea una ventaja competitiva usando Módulos de Seguridad de Hardware (HSM).
Get the ebookProtege el Internet de las Cosas Médicas (IoMT)
Descubre cómo las empresas biotecnológicas pueden proteger los dispositivos IoMT y encontrar el equilibrio perfecto entre agilidad, resiliencia y seguridad.
Get the solution briefAgilidad en un mundo post-cuántico
Cómo asegurar la agilidad criptográfica en la era post-cuántica.
Watch on-demand